Top Tools for Detecting and Preventing Man-in-the-Middle (MitM) Attacks
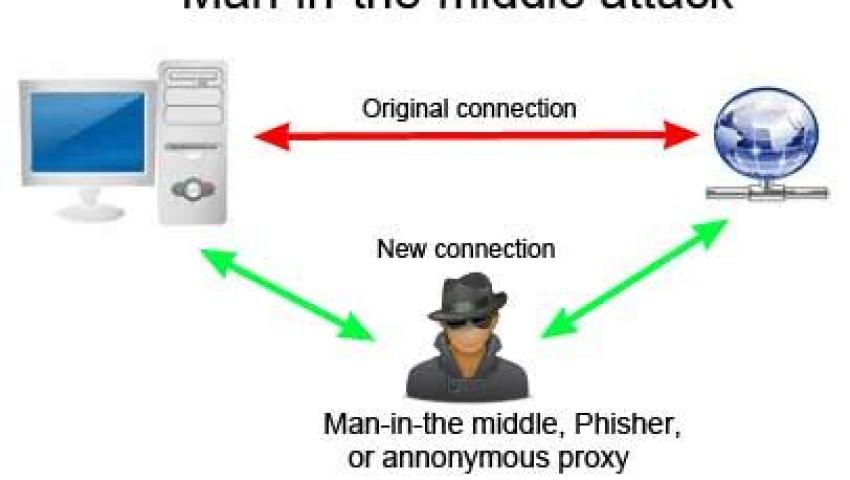
A Man-in-the-Middle (MitM) attack occurs when an attacker secretly intercepts and possibly alters the communication between two parties who believe they are directly communicating with each other. The attacker can then use this position to steal sensitive data, inject malicious code, or even impersonate one of the communicating parties...
Man-in-the-Middle (MitM) attacks have become increasingly prevalent as cybercriminals target vulnerabilities in communications to intercept or manipulate data. These attacks can take many forms, such as eavesdropping on sensitive communications, injecting malicious content, or impersonating a trusted entity to steal personal information. Preventing and detecting MitM attacks is critical for securing communications across networks, especially for organizations handling sensitive data like login credentials, payment information, or private communications.
In this article, we will explore the top tools that can help detect and prevent MitM attacks. These tools range from network monitoring and encryption solutions to advanced security protocols and techniques for ensuring safe communication channels. We’ll go over the tools' functionalities and provide practical examples to illustrate their use.
What is a Man-in-the-Middle (MitM) Attack?
A Man-in-the-Middle (MitM) attack occurs when an attacker secretly intercepts and possibly alters the communication between two parties who believe they are directly communicating with each other. The attacker can then use this position to steal sensitive data, inject malicious code, or even impersonate one of the communicating parties.
There are several common types of MitM attacks, including:
- Packet Sniffing: The attacker intercepts packets traveling through the network and analyzes them for valuable information.
- Session Hijacking: The attacker steals a session token to impersonate a legitimate user and gain unauthorized access to resources.
- SSL Stripping: The attacker downgrades a secure HTTPS connection to an insecure HTTP connection, allowing them to intercept and modify data.
How to Detect and Prevent MitM Attacks
To effectively prevent or detect MitM attacks, several tools and techniques can be employed. These tools include network sniffers, intrusion detection systems (IDS), encryption protocols, and more.
1. Wireshark: Network Traffic Analyzer
Wireshark is one of the most widely used network protocol analyzers. It allows you to capture and inspect packets on a network in real-time, making it an essential tool for detecting potential MitM attacks.
Features:
- Packet Capturing: Wireshark can capture network traffic in detail, including headers, payloads, and protocols used, making it easy to spot irregular traffic patterns.
- Protocol Analysis: It supports deep inspection of protocols such as HTTP, DNS, SSL/TLS, and more, which is crucial for identifying potential MitM manipulation.
- Filtering: You can filter captured packets based on specific criteria, such as IP addresses, protocols, or specific strings, helping to identify unusual activity or malicious traffic.
Example Use Case:
Imagine you’re a network administrator, and you suspect a MitM attack targeting your network. By using Wireshark, you can capture traffic on your network and look for suspicious signs like:
- Unencrypted communications on HTTP that should be using HTTPS.
- Unexpected SSL certificate errors.
- Out-of-place IP addresses or unusual DNS resolutions indicating potential DNS spoofing.
2. SSL Labs' SSL Test: Ensuring Secure Connections
When it comes to protecting against MitM attacks, SSL/TLS encryption is one of the best defenses. SSL Labs' SSL Test is an online tool that helps you analyze your website’s SSL/TLS configuration to ensure it’s secure and resistant to downgrade attacks.
Features:
- SSL Certificate Validation: SSL Labs’ SSL Test checks the configuration of SSL certificates, ensuring they are correctly configured to prevent interception.
- Protocol Version Detection: The tool identifies which versions of TLS/SSL are supported and ensures older, vulnerable protocols (e.g., SSLv3) are not in use.
- Cipher Suite Analysis: It checks the strength of the encryption ciphers used for data exchange, preventing attackers from exploiting weak ciphers for interception.
Example Use Case:
Imagine you're a website owner who wants to ensure your site is secure against SSL stripping or downgrade attacks. By running SSL Labs' SSL Test, you can verify that your site uses up-to-date protocols like TLS 1.2 or TLS 1.3 and employs strong ciphers, making it harder for attackers to intercept or alter communications.
3. Suricata: Intrusion Detection System (IDS)
Suricata is a high-performance, open-source Intrusion Detection and Prevention System (IDS/IPS) that can detect various types of attacks, including MitM attacks. Suricata analyzes network traffic and can alert administrators when suspicious activities or anomalies are detected.
Features:
- Deep Packet Inspection (DPI): Suricata can analyze packet contents, allowing it to detect MitM activities like packet injection or DNS spoofing.
- Multi-Protocol Detection: It supports detecting attacks across multiple protocols, including HTTP, DNS, and SSL/TLS.
- Real-Time Alerts: Suricata generates alerts for network traffic that exhibits suspicious patterns indicative of an active MitM attack.
Example Use Case:
You’re a network security administrator for a large enterprise. By deploying Suricata, you can monitor network traffic in real time and receive alerts about potential MitM attempts, such as suspicious SSL/TLS downgrade attempts or DNS spoofing attacks.
4. MITMf (Man-in-the-Middle Framework): Penetration Testing Tool
MITMf is a powerful framework for conducting MitM penetration tests, allowing security professionals to simulate MitM attacks and test the vulnerability of systems to such threats.
Features:
- SSL Stripping: MITMf allows security testers to simulate SSL stripping attacks to see if a target system is vulnerable to insecure communications.
- Credential Harvesting: It can capture usernames, passwords, and other sensitive data sent over the network, which is a core component of many MitM attacks.
- Manipulation of Traffic: It can manipulate network traffic to inject malicious payloads, modify content, and simulate data breaches.
Example Use Case:
As a penetration tester, you use MITMf to test a client’s internal network. You deploy MITMf on the network, intercepting and modifying traffic between a client and a web server. You test whether SSL stripping is successful by downgrading HTTPS traffic to HTTP and seeing if sensitive information is exposed.
5. Cain & Abel: Password Recovery Tool and MitM Attacks
Cain & Abel is a popular password recovery and network sniffing tool that is often used for MitM attacks. While it’s often associated with password recovery, it also has the capability to perform ARP spoofing, which is a common technique used in MitM attacks.
Features:
- ARP Spoofing: Cain & Abel can perform ARP spoofing (also known as ARP poisoning), tricking devices into sending traffic through the attacker’s machine for interception.
- Packet Sniffing: It can capture passwords and other sensitive information sent across a network, making it effective for detecting unencrypted traffic.
- Traffic Analysis: It allows you to analyze intercepted traffic to spot instances of MitM manipulation or sensitive data exposure.
Example Use Case:
As a network administrator, you notice slow performance on your network and suspect a MitM attack. You run Cain & Abel to perform ARP spoofing, tricking devices into redirecting their traffic through your machine. By inspecting the captured traffic, you can determine if attackers are stealing sensitive data or injecting malicious content.
6. OpenSSL: Secure Your Connections with Encryption
While not a direct detection tool, OpenSSL is an essential toolkit for securing network communications against MitM attacks by enabling encryption and certificate management. OpenSSL helps ensure that your servers and applications are using strong encryption protocols and certificates.
Features:
- Generate SSL Certificates: OpenSSL allows administrators to create their own SSL certificates for encrypting data.
- Verify Certificate Authenticity: It can be used to verify whether SSL certificates are valid and not subject to being spoofed.
- Encrypt Traffic: It helps secure communication channels by enabling strong encryption, preventing unauthorized parties from tampering with the data.
Example Use Case:
As an administrator, you use OpenSSL to generate a new SSL certificate for your web server and configure it to use strong TLS protocols. This ensures that communications between your website and users are encrypted and protected from MitM attacks.
7. DNSSEC: Protect DNS from Spoofing
DNSSEC (Domain Name System Security Extensions) is a suite of extensions to DNS that helps prevent MitM attacks targeting the DNS system. DNSSEC works by signing DNS data, ensuring the integrity and authenticity of DNS responses.
Features:
- Authentication of DNS Responses: DNSSEC ensures that DNS responses cannot be tampered with by attackers attempting to redirect users to malicious websites.
- Prevents Cache Poisoning: By using cryptographic signatures, DNSSEC prevents attackers from poisoning the DNS cache with fraudulent entries.
Example Use Case:
As a website owner, you implement DNSSEC to protect your domain from DNS spoofing attacks, ensuring that users always reach the legitimate version of your website and not a fake one set up by attackers.
Conclusion
MitM attacks pose a serious threat to network security, but with the right tools, these attacks can be detected and prevented. Using network monitoring tools like Wireshark and Suricata, implementing secure communication protocols through SSL/TLS (tested by SSL Labs’ SSL Test), and leveraging specialized tools like MITMf and Cain & Abel for penetration testing can help identify vulnerabilities and protect your network from these types of attacks. Additionally, encryption frameworks like OpenSSL and DNS security features like DNSSEC further bolster defenses against MitM threats. By utilizing a combination of these tools, organizations can ensure the security of their communications and protect against malicious interception and manipulation.
Alex Ananenko
Leave a comment
Your email address will not be published. Required fields are marked *


