Best Tools for DDoS Attack Simulation and Testing
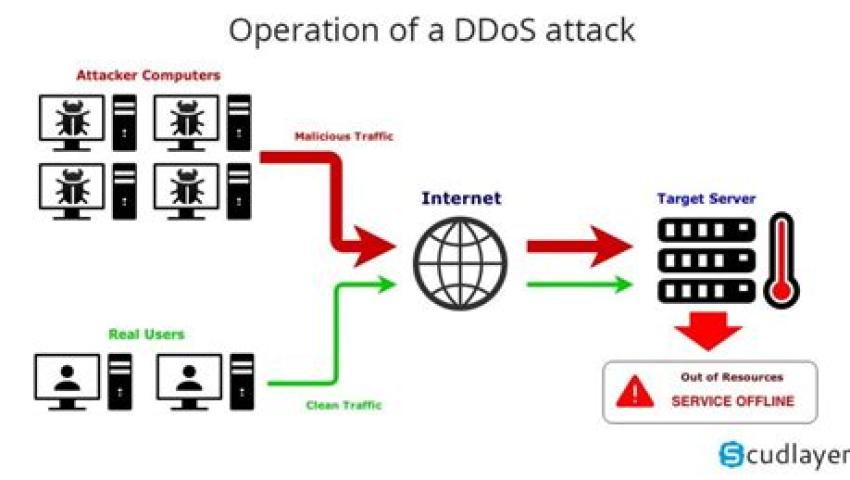
Distributed Denial of Service (DDoS) attacks are one of the most common and disruptive forms of cyberattacks in today’s digital world. These attacks involve overwhelming a targeted system, such as a website or online service, with a massive volume of traffic, rendering it inaccessible to legitimate users.
The increasing frequency and sophistication of DDoS attacks have made it essential for organizations to test their resilience against such threats. DDoS attack simulation and testing tools are invaluable for assessing and fortifying network security against these attacks.
In this article, we will discuss some of the best tools available for DDoS attack simulation and testing, how they work, and provide step-by-step examples of how to use them.
1. LOIC (Low Orbit Ion Cannon)
LOIC (Low Orbit Ion Cannon) is one of the most well-known tools for DDoS simulation. It is an open-source tool that allows users to send HTTP, TCP, and UDP floods to a target. Originally designed for stress-testing purposes, LOIC has also been used by hackers to launch attacks.
Key Features:
Simple to Use: LOIC has a user-friendly interface that allows even novice users to execute DDoS attacks.
Customizable Attack Types: You can choose between various attack methods, including TCP, UDP, and HTTP flood attacks.
- Control Over Attack Parameters: Users can set parameters like attack duration, target IP, and the number of threads used.
How to Use LOIC:
Download LOIC from the official repository or trusted websites.
Launch the tool and input the target IP address of the system or website you want to test.
Select the attack type (TCP, UDP, or HTTP).
Configure attack parameters: Set the number of threads (higher numbers mean more simultaneous connections), and define the attack duration.
- Start the attack: Click "IMMA CHARGIN MAH LAZER" to begin the simulation.
LOIC is best used for small-scale, basic DDoS simulations, primarily for educational purposes. It is not recommended for testing live production systems without explicit permission, as it can inadvertently disrupt the target.
2. Hping3
Hping3 is a network tool that can be used to generate TCP, UDP, ICMP, and RAW-IP packets to simulate DDoS attacks. It is highly flexible and often used by security professionals to test network security.
Key Features:
Advanced Protocol Simulation: Hping3 can simulate traffic for multiple protocols, making it more versatile than simpler tools.
Customizable: You can fine-tune packet sizes, flags, and other parameters to simulate complex DDoS attacks.
- Stealth Attacks: Hping3 can create attack packets that mimic legitimate traffic, making it difficult for traditional defense mechanisms to detect.
How to Use Hping3 for DDoS Simulation:
Install Hping3 on your Linux system. It is often included in the default repository, so you can install it using:
sudo apt install hping3Launch a basic attack: To simulate a simple SYN flood (one of the most common DDoS attack types), run the following command:
sudo hping3 --flood --syn -p 80 target_ipThis command sends a flood of SYN packets to port 80 of the target system, mimicking a SYN flood attack.
Customize Attack Parameters: To adjust the attack parameters, modify the flags. For example, you can change the target port or use different packet types. The command below floods port 443 with a mixture of SYN and RST packets:
sudo hping3 --flood --syn --rst -p 443 target_ip
Hping3 is ideal for more advanced users who require precise control over the parameters of their simulated attacks. It can be used for both small- and large-scale attack simulations.
3. Xerxes
Xerxes is a lightweight, command-line DDoS tool that is primarily used to simulate HTTP flood attacks. It was designed for simplicity and speed, allowing users to send thousands of HTTP requests to a server in a very short amount of time.
Key Features:
Fast and Simple: Xerxes is specifically designed for HTTP flood attacks, making it a great choice for simulating attacks on web servers.
Minimal Setup: There is no need to configure complex parameters. You simply input the target URL and let the tool do the rest.
- Lightweight: It uses minimal resources, so it can be run on relatively low-powered machines.
How to Use Xerxes for DDoS Simulation:
- Download Xerxes from a trusted source.
- Open a terminal and navigate to the Xerxes directory.
Compile the tool if required:
g++ xerxes.cpp -o xerxesRun the attack by providing the target URL and the desired number of requests:
./xerxes http://targetwebsite.com- Monitor the attack: Xerxes will continuously send HTTP requests to the target, simulating an HTTP flood attack.
Xerxes is a great tool for simulating high-traffic HTTP-based attacks, but it is limited to HTTP flood simulations. It is most effective for testing web servers or websites against such attacks.
4. Slowloris
Slowloris is a unique tool designed to simulate HTTP-based DDoS attacks, specifically targeting web servers that rely on persistent connections. Slowloris works by holding connections open and sending partial HTTP requests to exhaust server resources, ultimately causing the server to fail.
Key Features:
Focus on HTTP Floods: Slowloris is specifically crafted to simulate slow HTTP attacks, making it a great choice for testing web server resilience.
Lightweight: The tool uses very little bandwidth but can still bring down servers by consuming resources slowly over time.
- Server-side Impact: Slowloris simulates long-lasting attacks that put strain on server resources without flooding the network with excessive traffic.
How to Use Slowloris for DDoS Simulation:
Install Slowloris: Clone the repository from GitHub:
git clone https://github.com/gkbrk/slowloris.gitNavigate to the Slowloris directory:
cd slowlorisRun the tool:
python2 slowloris.py targetwebsite.comSlowloris will begin sending partial HTTP requests to the server, tying up resources and making it slow or unavailable.
Slowloris is effective for testing how well a web server can handle slow HTTP-based attacks, which are often used to avoid detection by traditional DDoS defenses.
5. Pentesters Toolkit - DDoS Simulator
The Pentesters Toolkit DDoS Simulator is a more advanced tool that allows penetration testers to simulate large-scale DDoS attacks, including SYN floods, UDP floods, HTTP floods, and DNS amplification attacks.
Key Features:
Comprehensive Attack Simulation: The toolkit supports multiple DDoS attack vectors and can simulate a variety of scenarios, including amplification attacks and SYN floods.
Scalability: You can simulate attacks on a large scale, making it suitable for testing robust enterprise-level networks.
- Easy to Use: It comes with a user-friendly GUI, making it accessible for both beginners and advanced users.
How to Use the DDoS Simulator:
Download the toolkit and install it on your system.
Launch the tool and select the type of DDoS attack you wish to simulate, such as SYN Flood.
Configure the target information: Enter the target IP address and specify parameters like attack duration and traffic volume.
- Initiate the attack: Click the “Start” button to launch the simulation.
This tool is highly effective for simulating attacks against large, enterprise-scale networks, helping to test DDoS defenses in more complex environments.
Conclusion
DDoS attack simulation and testing tools are invaluable for understanding the vulnerabilities of systems and networks in the face of high-volume traffic. The tools mentioned in this article—LOIC, Hping3, Xerxes, Slowloris, and Pentesters Toolkit DDoS Simulator—offer a range of functionalities, from simple flood simulations to more advanced and stealthy attack methods. Each tool is suited for different types of DDoS attack simulations, so the choice of tool should depend on the specific needs of your testing environment.
When conducting DDoS testing, it is crucial to always have proper authorization and to ensure that your actions do not negatively affect other systems or networks. Using these tools responsibly will help you better prepare your network defenses and improve your security posture against the ever-evolving threat of DDoS attacks.
Alex Ananenko
Leave a comment
Your email address will not be published. Required fields are marked *


